Diese Kunden
arbeiten bereits mit deskMate
arbeiten bereits mit deskMate
deskMate Rechenzentren
Da wo unsere Kunden Sie benötigen
Da wo unsere Kunden Sie benötigen
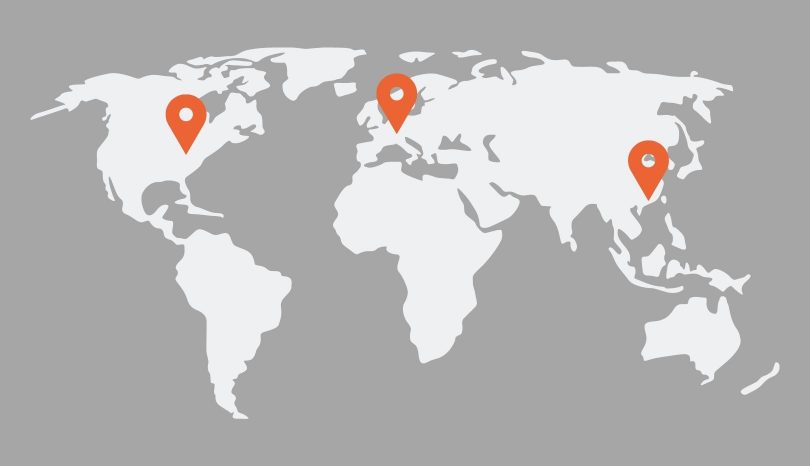
Vint Hill / USA | Frankfurt / Deutschland | Hong Kong / VR China
Nachhaltig und umweltbewusst

Nachhaltigkeit und Umweltbewusstsein haben einen sehr hohen Stellenwert in unseren Unternehmenszielen.
Unser Bürogebäude ist CO-2 neutral und unser Hauptrechenzentrum in Frankfurt wird zu 100% mit Ökostrom betrieben. Unser Fuhrpark fährt zu 100% elektrisch oder teilelektrisch.
Dabei wollen wir es aber nicht belassen, sondern arbeiten kontinuierlich daran, noch besser mit Ressourcen umzugehen und unseren ökologischen Fußabdruck so weit wie möglich zu minimieren.
Ausgezeichnet von
führenden Spezialisten weltweit
führenden Spezialisten weltweit







